인프라
신규 엘라스틱 서치 설치 본문

#vi /etc/elasticsearch/elasticsearch.yml

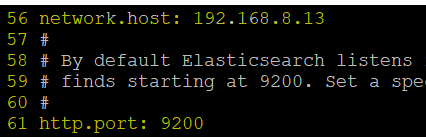

# 서비스 시작

자바로 동작 확인


[root@node ~]# curl -XGET --cacert /etc/elasticsearch/certs/http_ca.crt --user "elastic:N92bVcCuqUEybkZTVUBf" "https://node.kitri.com:9200"
[root@node ~]# curl -XGET --cacert /etc/elasticsearch/certs/http_ca.crt --user "elastic:N92bVcCuqUEybkZTVUBf" "https://node.kitri.com:9200/_cat/nodes"
192.168.8.13 67 68 95 4.58 3.73 3.82 cdfhilmrstw * node.kitri.com

msfadmin@metasploitable:~$ mysql -u root
mysql> USE dvwa;

mysql> SELECT MD5('1234');
+----------------------------------+
| MD5('1234') |
+----------------------------------+
| 81dc9bdb52d04dc20036dbd8313ed055 |
+----------------------------------+
1 row in set (0.00 sec)mysql> update users SET password = MD5('1234') WHERE user_id=1;
Query OK, 1 row affected (0.00 sec)
Rows matched: 1 Changed: 1 Warnings: 0
mysql> update users SET password = MD5('3333') WHERE user_id=2;
Query OK, 1 row affected (0.00 sec)
Rows matched: 1 Changed: 1 Warnings: 0

>>> import requests
>>> user = 'admin'
>>> pass1 = '1212'
>>> pass2 = '1234'
>>> url = f'http://metas/dvwa/vulnerabilities/brute/?username={user}&password={pass1}&Login=Login'
>>> url1 = f'http://metas/dvwa/vulnerabilities/brute/?username={user}&password={pass1}&Login=Login'
>>> url2 = f'http://metas/dvwa/vulnerabilities/brute/?username={user}&password={pass2}&Login=Login'
>>>
>>> response1 = requests.get(url1)
>>> file=open('url1.html', 'w', encoding='utf-8')
>>> file.write(response1.text)
1289
>>> file.close()
>>> response2 = requests.get(url2)
>>> file=open('url2.html', 'w', encoding='utf-8')
>>> file.write(response2.text)
1289
>>> file.close()
>>> import requests
>>> user = 'admin'
>>> pass1 = '1212'
>>> pass2 = '1234'
>>>
>>> url1 = f'http://192.168.8.12/dvwa/vulnerabilities/brute/?username={user}&password={pass1}&Login=Login'
>>> url2 = f'http://192.168.8.12/dvwa/vulnerabilities/brute/?username={user}&password={pass2}&Login=Login'
>>>
>>> response1 = requests.get(url1)
>>> file=open('url1.html', 'w', encoding='utf-8')
>>> file.write(response1.text)
1289
>>> file.close()
>>> response2 = requests.get(url2)
>>> file=open('url2.html', 'w', encoding='utf-8')
>>> file.write(response2.text)
1289
>>> file.close()
'Network' 카테고리의 다른 글
| Blind SQL 인젝션 (0) | 2022.11.23 |
|---|---|
| 엘라스틱 서치(2) - metricbeat (0) | 2022.11.16 |
| DVWA - XSS (Cross site scripting) (0) | 2022.11.14 |
| hydra 히드라 (0) | 2022.11.07 |
| MSF 보조 기능 (0) | 2022.11.04 |
Comments




